- Solutions
- For Industry
- By Need
- Products
- VarbaseEnterprise CMS Distribution for Drupal
- Uber PublisherEnterprise Digital Media Platform Builder
- VardocDrupal Knowledge Base Platform
- Campaign StudioOpen Marketing Platform - by Acquia
- Open SocialSocial Business Platform - by Open Social
- Services
- Strategy
- Design
- Development
- Migration
- Support and MaintenanceSupport and Maintenance
- DevOps
- Digital Marketing

Datasheet
- Clients
- Ideas
- About
- Contact Us

Drupal Security: The Complete Guide

For corporates in the finance vertical and especially for government agencies, high-security standards are a critical factor when selecting their CMS platform. For banks, their reputation and credibility are at stake if they are unable to secure their clients’ personally identifiable information (PII). For government agencies, it may be PII and highly sensitive information that needs to be kept secure from potential cyber-attacks.
This article will give a top-line view of Drupal’s website security best practices and demonstrate why many banks and government agencies use Drupal for their CMS requirements.
Is Drupal Secure?
Drupal has a reputation for good security protocols that are supported by the fact that over 150 government agencies worldwide have selected it for their CMS. More quantitative data highlighted in a recent Website Threat Report by Sucuri backs up Drupal’s image as a good option for cybersecurity best practices.
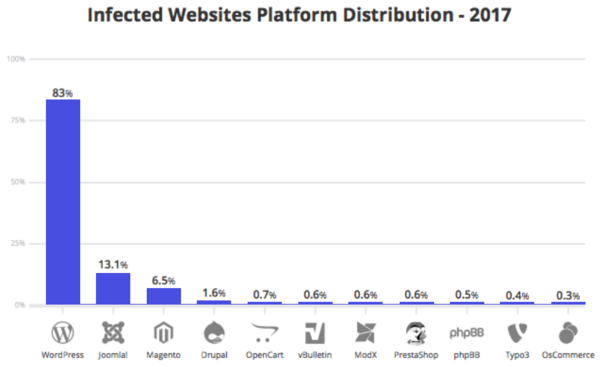
It is risky to claim that any technology is completely secure but Drupal’s track record shows that it consistently outperforms every other CMS option when it comes to security.
Frequently asked questions
Does Drupal have processes in place for addressing security vulnerabilities?
Drupal adheres to the (Open Web Application Security Project) OWASP standards outlined in their OWASP Application Security Verification Standard (OASVS). This standard aims to normalize web application security verification and provide ways to test application security controls.
In addition, Drupal’s API currently validates data to avoid, cross-site scripting (XSS), injection, cross-site request forgeries (CSRF), and also supplies session management.
Is open-source software secure?
Although it is a common belief that open source is less secure than proprietary software, in reality, this is not always the case. Security levels are not better in all proprietary software options or worse in all open source options. It is specific to the technology and its own best practice protocols.
Who manages and updates Drupal’s security protocols?
Drupal has an all-volunteer security team whose job is to resolve all security issues at a Security Advisory level. They also provide an update of all publicly available security documentation for developers writing code or practicing cybersecurity and help the Drupal infrastructure secure.
Drupal security best practices
Run by the security team, Drupal 7’s security protocols have been improved again in Drupal 8. This continuous improvement approach ensures that the approach to cybersecurity is always current and most importantly, relevant.
At a structural level, Drupal has a multi-layered cache architecture which helps to prevent DDOS attacks as well as being able to scale with your traffic growth. It also offers customizable database encryption that can be configured site-wide or by sections like content type or nodes.
Drupal’s API is designed to prevent many cross-site hacks and also to manage login attempts from single IPs within a certain time frame, helping to prevent brute-force password attacks.
With the rollout of Drupal 8, came two key security upgrades. Firstly, the PHP input format was removed from the core which has helped to minimize code execution vulnerabilities. The other innovation was the introduction of Twigs templates that have improved the validation of 3rd party themes which are traditionally the most exploited vulnerability in CMSs.
Varbase security features
Available on GitHub, the Varbase core module bundles together several security features.
These include:
- Captcha and ReCaptcha for spam prevention
- The configurable password policy module
- Security kit module for various external threat mitigation and SSL/TSL security
- Username enumeration prevention for reducing existing user name exploitation
Learn Why Varbase CMS Is the Best Multilingual Enterprise-Grade Drupal Website Builder
Consider Drupal for security
Website security, sensitive information protection, and guarding your customer's information are vital in the online landscape. Often your reputation and client base are dependent on maintaining high-security standards and preventing breaches.
Drupal 8 advancements in line with its Drupal Cybersecurity focus have produced a highly flexible and secure open-source CMS.
Want to find out more about Drupal or need to secure your online properties? Let’s get you started.
- Security
- Drupal
- Drupal 8
- Drupal 9



